Online and at conferences, people ask me how to get started in threat intel. What I usually offer as advice to budding analysts starting out is to practise analysing things in the wild. And by ‘analysing things in the wild’ I mean looking for live reports of cybercriminal activity by others online. One of my favourite examples is SMS phishing text messages, also called Smishing scams.
It is a commonly held view that new analysts learn best by doing. It also does not matter if you are not the first to report on something. New analysts should not worry about that, as long as they do a bit of OSINT at least to confirm they do not accidentally say they are the first and only researcher to find whatever it is they found. In my experience, there are always organizations and teams with more experience and telemetry than you. It’s just that they did not report on it publicly (yet). This goes for even the top research teams at incident response or antivirus companies. Not “being first” shouldn’t discourage you from sharing your research. More is better.
Practising threat research by looking at SMS phishing texts is a great first time thing for new analysts. This is because it takes no time at all to find these in the wild and due to the sheer volume of them you are quite likely to be the first to share something on it. You can go to Twitter or other social media platforms and simply search “scam text” and find reports by general users immediately. Every other day there is a new wave of scam text messages, giving any analyst an opportunity to breakdown a campaign and provide useful and actionable intelligence for no cost other than some of their time.
Below is an example of an SMS phishing text that I found on Twitter on one rainy Saturday afternoon after BSides Basingstoke.
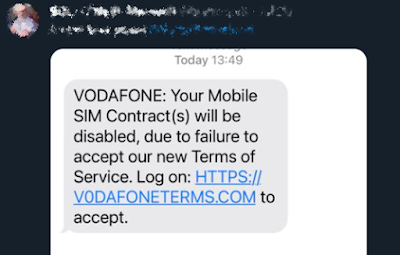
Going to this phishing page on a PC was not possible, however, nor was visiting it via a service like URLscan. I later realized that this was because it was using Cloudflare’s service called “Bot Fight Mode”. This legit and free service that is designed to prevent bot devices from visiting websites and, in this case, only non-emulated mobile devices. This setting means that any visitor that isn’t on a non-emulated mobile device is shown a 404 Not Found HTTP error message instead.

However, once the scam page is loaded up on a valid mobile device, it will reveal itself. If clicked by a target user, they are presented with a fake login page posing as the My Vodafone service. If some fake data is entered, it is possible to step through the phishing kit without giving the attacker any real information whilst also understanding the features of the scam.

1. It will ask you to login.
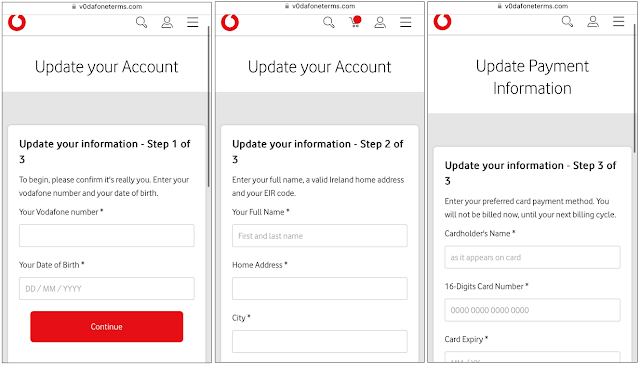
2. And update your Account and Payment Information.

3. And then get you to select which bank is your and then redirect you.
The above three image are what you will see if you visit the page and enter fake data. In theory, once a victim enters their personal information, such as their Vodafone customer details, name, address, and credit card details, the phishers have a comprehensive dataset to defraud their target.
The scam does not end their though. What may start as a Vodafone-themed scam turns into a classical bank credential phishing scheme. In this instance, all the banks are located in Ireland. These details banking details appear to be the ultimate end goal of the adversary that created this phishing site.
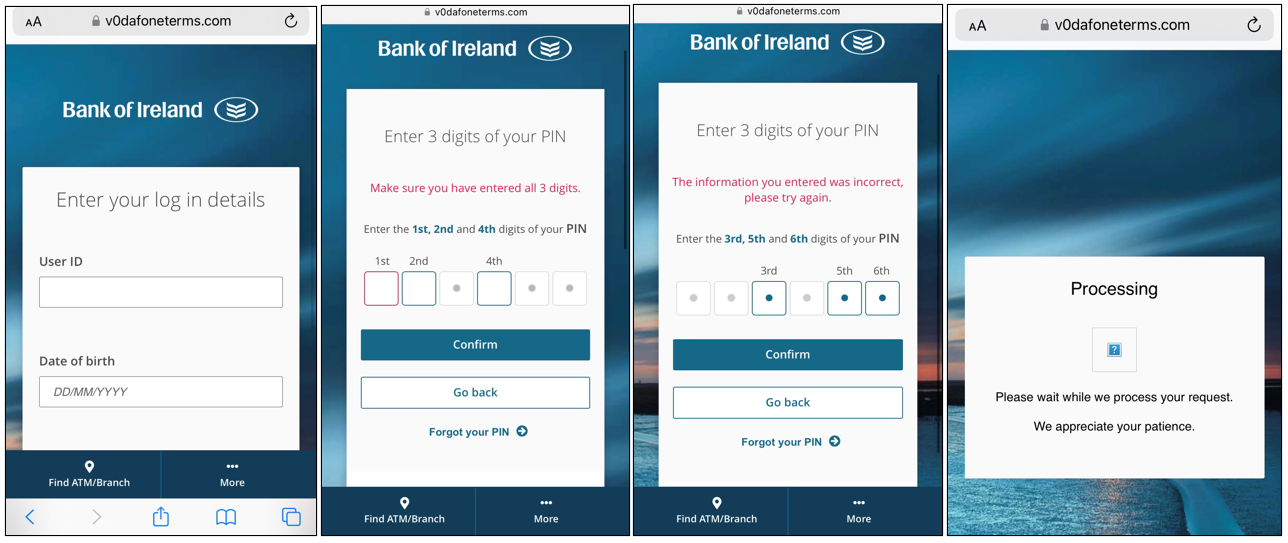
If the target user enters their details and selects a bank from the dropdown list showed in step 3 above, they are then given a phishing page that poses as the login system for that bank, with logos and styling and all. These fake login pages also collect additional personal details and credentials for online consumer banking systems.

Further, with the data already collected from the Vodafone part of the scam, it could be possible for the scammers to establish some persistence by tricking the bank by impersonating the victim. This is because the adversary already has a lot of personal information collected about the victim – including the details that the bank may ask for to verify the user is who they say they are. This aspect of the scam makes this an interesting two-part attack that is a little bit more sophisticated than your usual fake login page that asks for a single set of credentials.
Now we understand the scam more, we can perform some open source intelligence (OSINT) infrastructure pivoting on the domain sent in the SMS phishing texts. By using the free Whois DomainTools app we can glean some additional context about the threat. This includes answering the following questions: When was it created? Who was it registered with? And where is it hosted?

The answers to the above three questions are in the screenshot. We can see it was created on 2023-07-19. It was registered with TUCOWS. And it is hosted with Cloudflare. This information is useful to us because now we know a bit more about the adversary’s behaviours and their choices. This information is also useful for taking action against the adversary, imposing a bit of cost to them. I submitted two takedown requests for the domain to TUCOWS and Cloudflare. It is not clear however if or when it will be taken down but both services say on their websites that they accept abuse reports against phishing sites.
Unfortunately, because this Vodafone-themed page is hosted on Cloudflare, there is not much use trying to pivot on its hosting server because of Cloudflare’s multi-tenancy and IP address allocation system for domains protected by its content delivery network (CDN). If you tried to pivot on this IP address in a tool like VirusTotal, all you would see is other Cloudflare customers, including valid and benign websites. Even if an analyst tried to pivot on the IP address of the Vodafone page in URLscan (which actually says it is on IPv6) it will not provide any additional related adversary infrastructure for this same reason.
What we can do, however, is a bit more pivoting on the phishing page’s characteristics. One of my favourite free tools for this is still URLscan. The first URL we encounter when visiting the My Vodafone page is “hxxps://v0dafoneterms[.]com/wc/lgn.php?user=true” (The URL is defanged to prevent readers from accidentally clicking it).
We can use URLscan to search for that same directory and filename path (“/wc/lgn.php”) in the URL. This is this because we can potentially uncover additional phishing pages with similar characteristics related to the same campaign or adversary. When I searched for the same path in the URL I found only one other submission to URLscan and it was a PayPal phishing site that was created recently as well.
We can assume with moderate confidence that it is likely related to either the same adversary who configured the My Vodafone phishing page or two adversaries using a similar phishing kit or phishing page setup guide. This is can remain as a hypothesis for now. Additional research is required to understand the precise reason for this technical overlap (but this is usually only possible with more telemetry and time to track it).
Additionally, it is also possible to pivot on the hosting infrastructure of that domain. This led me to a Ukrainian hoster that appears to have some Russian IP address space that had a large amount of phishing pages on it and not much else, making it potentially one to block pre-emptively.

The discovery of this Ukrainian phishing page hoster is a useful find. It is a new source to track the latest phishing campaigns and gain intelligence on who is being targeted and how. If you are a CTI analyst who works with or works for one of the banks, mobile carriers, or other organizations who is being impersonated it would be useful to track these adversaries and proactively perform takedown requests to stop customers being scammed, costing the organization money in refunds.
Hopefully to any new analyst who read this can follow along and learn something new!
Indicators of Compromise (IOCs)
- hxxps://v0dafoneterms[.]com/wc/lgn.php?user=true
- hxxps://v0dafoneterms[.]com/wc/error.php?user=true
- hxxps://v0dafoneterms[.]com/wc/info.php?user=true
- hxxps://v0dafoneterms[.]com/wc/info2.php?user=true
- hxxps://v0dafoneterms[.]com/wc/card.php?user=true
- hxxps://v0dafoneterms[.]com/wc/process.php?user=true
- hxxps://v0dafoneterms[.]com/wc/BO
- hxxps://v0dafoneterms[.]com/wc/PT
- hxxps://v0dafoneterms[.]com/wc/AI
- hxxps://v0dafoneterms[.]com/wc/AV
- hxxps://v0dafoneterms[.]com/wc/UL
- hxxps://v0dafoneterms[.]com/wc/KB


