Prologue
I find uncovering new campaigns and sharing research on novel threats is one the most enjoyable parts of my job as a CTI researcher. Especially the types of threats not many other researchers really spend much time investigating, or at least those who do rarely disclose their findings publicly. My investigation on the RedZei group is also an example of this.
Background
I have recently been investigating a financially motivated threat actor I’ve dubbed “GreenMwizi” that I believe to be from Kenya. They have setup a dozen fake Booking.com Twitter accounts and are currently targeting users who make public complaints. The main aim of these scammers is to socially engineer users over the phone into sending them funds via Remitly, an international money transfer service. By interacting with the scammers myself I was able to find out their phone number and trace their IP address and device information.
This type of activity is extremely common on Twitter. Users should always do their due diligence if they respond to an “official” account replying to them. Ever since Elon Musk decided to remove the blue verification icon from many official Twitter accounts, this issue has been exacerbated. Organizations whose users rely on Twitter to communicate with them should be proactively monitoring for these types of scammers to prevent them from being victimized. Now more so than ever, since Elon Musk’s Twitter is failing to respond to the bot issues such as this themselves.
About GreenMwizi Campaigns
This investigation started when a friend noticed one of the fake accounts replying to a user on Twitter. Here (see Figure 1) is an example of how this scam begins by a target being lured into the Twitter direct messages (DMs).
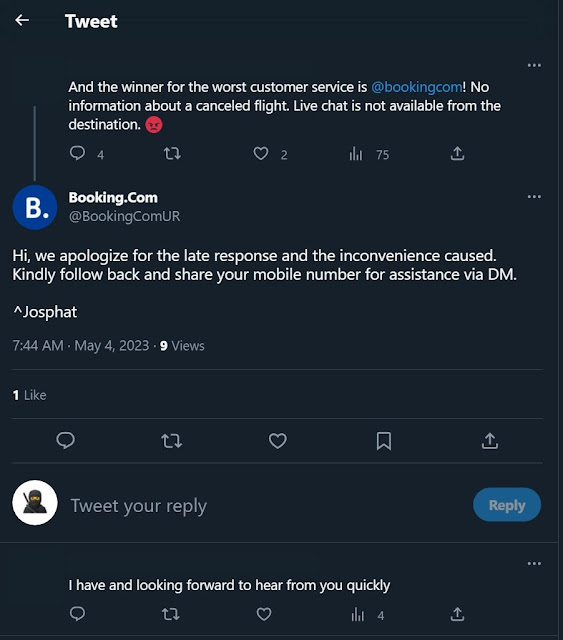
Figure 1: Booking.com scammer replies on Twitter
I decided I wanted to learn more about how this scam works. Whether the scammers send a phishing link or something. I’ve personally not come across Booking.com scammers before, but I can imagine credentials to an account could be used to steal information and fraud. So, to learn more, I DM’d the scammer after they replied to me.
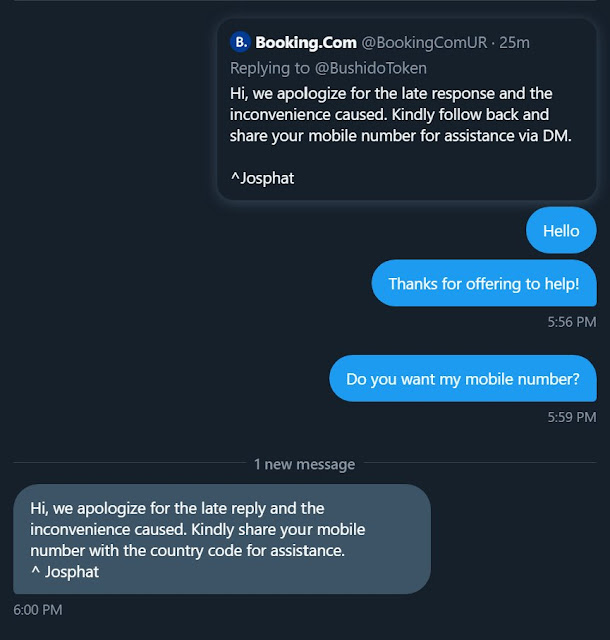
Figure 2: Twitter DMs with the scammer begin
I pretended to be having issues with Booking.com so I could see an example of what they say in the Twitter DMs. They asked for a phone number and asked to chat over WhatsApp and also for a Booking.com reference number. They then tried to call me via WhatsApp a couple times (see Figure 3), but I did not pick up at that time because I just wanted to get their phone number.

Figure 3: Two attempts at a WhatsApp call from the scammer
Notably, the threat actor’s mobile number had a +254 extension, which is for Kenya. Also, they had “Remitly ✅” in their WhatsApp status (see Figure 4). A quick Google Search found that Remitly is an international money transfer services, similar to Western Union or Wise.

Figure 4: Remitly was set as their WhatsApp status
Searching Twitter some more uncovered that this account was part of a dozen connected Twitter accounts all posing as Booking.com and replying to hundreds of Twitter users who have complained on the site (see Table 1). I noticed the reuse of the same text in replies and also the name “CJ” by several of these accounts in replies to users as well. Paired with the timing, I assessed with high confidence these are almost certainly under the control of the same adversary. Also, for the record, I have reported all of these to Twitter.
| Joined | URL | Name |
|---|---|---|
| February 2023 | https://twitter.com/__bookingcom_ | Mitchell |
| March 2023 | https://twitter.com/bookingcom_2 | CJ |
| March 2023 | https://twitter.com/bookingcomm | |
| March 2023 | https://twitter.com/ibookingcom | Ha |
| March 2023 | https://twitter.com/booking_com2 | CJ |
| March 2023 | https://twitter.com/bookingcomdesk | CJ or GL or Tz |
| April 2023 | https://twitter.com/bookingcom_A | Jm or SH |
| April 2023 | https://twitter.com/1_bookingcom | |
| April 2023 | https://twitter.com/BookingComUR | Josphat |
| May 2023 | https://twitter.com/bookingc0m__ | MJ |
| May 2023 | https://twitter.com/bookingcomla | Ferguson |
| May 2023 | https://twitter.com/bookkingcom |
Table 1: An array of recently created fake Booking.com Twitter accounts
Another interesting thing I noticed was that one of the fake Booking.com accounts also had the wrong Twitter bio. This one was instead related to MoneyGram, which is potentially another type of scam this adversary runs.

Figure 5: MoneyGram-themed fake Booking.com account
Tracing GreenMwizi
By doing a little social engineering of my own against the scammers, I was able to get detailed device information from their mobile phone, further confirming their location to be in Kenya (see Table 2).
| Type | Device Information |
|---|---|
| IP Address | 154.123.56.191 |
| Country | Kenya, Nairobi |
| Browser | Chrome Mobile (94.0.4606.85) |
| Operating System | Android 11 |
| Device | Infinix Hot 12i |
| User Agent | Mozilla/5.0 (Linux; Android 11; Infinix X665) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.85 Mobile Safari/537.36 |
| Host Name | kiboko.telkom.co.ke |
| ISP | JAMBONET |
| Phone Number | +254 771 609283 |
Table 2: Threat actor’s device information
Finally, to summarize what I’ve uncovered about GreenMwizi’s campaign so far, I used the Diamond Model. Seeing as this specific campaign has not yet been covered yet in open sources, as it is fairly new, I created this model to hopefully help other researchers and analysts track them.
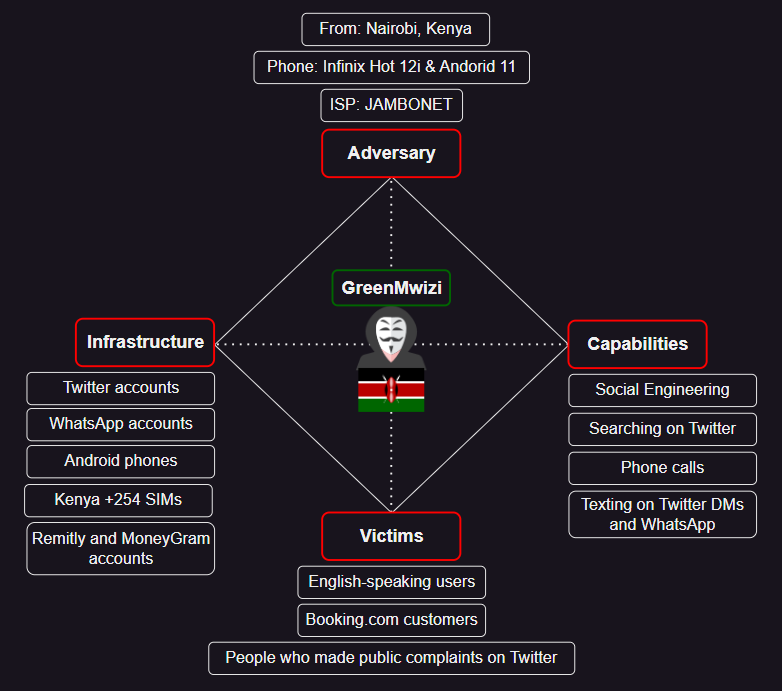
Figure 6: GreenMwizi Diamond Model
Courses of Action
To impose cost against these threat actors, I would recommend that:
- Twitter takes down these Booking.com impersonating accounts and bans the threat actor’s registration details, such as phone numbers, IP addresses, or email addresses
- Mobile carriers should also block the GreenMwizi phone number
- WhatsApp should take down the Booking.com impersonating accounts
- Remitly should use the provided device information from Table 2 to search for the scammer’s account and shut it down
- Victims of GreenMwizi style scams should also report them to law enforcement who can begin the process of building a case against GreenMwizi


