ophisticated cyberattacks targeting some of the most secure networks globally have been carried out by Advanced Persistent Threat (APT) groups. Many of these groups operate on behalf of national intelligence agencies or military forces, while others may be private hacking groups hired for specific missions. An APT group is skilled at gaining access to a […]
Category Archives: Uncategorized
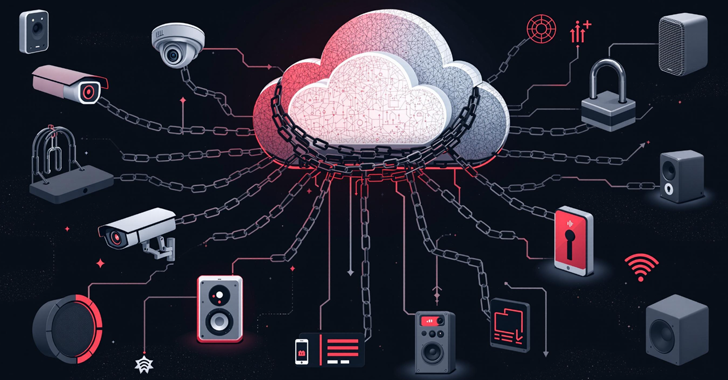
“The cloud is not a physical entity, but instead is a vast network of remote servers around the globe which are linked together and meant to operate as a single ecosystem. These servers are designed to either store and manage data, run applications or deliver content or a service such as streaming videos, web email, […]
One effective way to enhance your OSINT skills is through consistent practice. As the saying goes, practice makes perfect. One way to improve your OSINT skills is to practice. Practice makes perfect as they say. https://platform.twitter.com/embed/Tweet.html?dnt=false&embedId=twitter-widget-1&features=eyJ0ZndfdGltZWxpbmVfbGlzdCI6eyJidWNrZXQiOltdLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X2ZvbGxvd2VyX2NvdW50X3N1bnNldCI6eyJidWNrZXQiOnRydWUsInZlcnNpb24iOm51bGx9LCJ0ZndfdHdlZXRfZWRpdF9iYWNrZW5kIjp7ImJ1Y2tldCI6Im9uIiwidmVyc2lvbiI6bnVsbH0sInRmd19yZWZzcmNfc2Vzc2lvbiI6eyJidWNrZXQiOiJvbiIsInZlcnNpb24iOm51bGx9LCJ0ZndfZm9zbnJfc29mdF9pbnRlcnZlbnRpb25zX2VuYWJsZWQiOnsiYnVja2V0Ijoib24iLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X21peGVkX21lZGlhXzE1ODk3Ijp7ImJ1Y2tldCI6InRyZWF0bWVudCIsInZlcnNpb24iOm51bGx9LCJ0ZndfZXhwZXJpbWVudHNfY29va2llX2V4cGlyYXRpb24iOnsiYnVja2V0IjoxMjA5NjAwLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X3Nob3dfYmlyZHdhdGNoX3Bpdm90c19lbmFibGVkIjp7ImJ1Y2tldCI6Im9uIiwidmVyc2lvbiI6bnVsbH0sInRmd19kdXBsaWNhdGVfc2NyaWJlc190b19zZXR0aW5ncyI6eyJidWNrZXQiOiJvbiIsInZlcnNpb24iOm51bGx9LCJ0ZndfdXNlX3Byb2ZpbGVfaW1hZ2Vfc2hhcGVfZW5hYmxlZCI6eyJidWNrZXQiOiJvbiIsInZlcnNpb24iOm51bGx9LCJ0ZndfdmlkZW9faGxzX2R5bmFtaWNfbWFuaWZlc3RzXzE1MDgyIjp7ImJ1Y2tldCI6InRydWVfYml0cmF0ZSIsInZlcnNpb24iOm51bGx9LCJ0ZndfbGVnYWN5X3RpbWVsaW5lX3N1bnNldCI6eyJidWNrZXQiOnRydWUsInZlcnNpb24iOm51bGx9LCJ0ZndfdHdlZXRfZWRpdF9mcm9udGVuZCI6eyJidWNrZXQiOiJvbiIsInZlcnNpb24iOm51bGx9fQ%3D%3D&frame=false&hideCard=false&hideThread=false&id=1304106646822686720&lang=en-gb&origin=https%3A%2F%2Fblog.bushidotoken.net%2F2020%2F09%2Fosint-challenge-key-west.html&sessionId=edc410e1d1b16a0a1cc9686dbff34ef8b8cd79b4&theme=light&widgetsVersion=2615f7e52b7e0%3A1702314776716&width=550px Thanks @JakeCreps, I’ll take it from here. Let’s start by visiting the stream, the initial piece of intelligence provided: I immediately […]
I recently discovered a phishing command and control (C&C) Simple Mail Transfer Protocol (SMTP) server hosted on the same page where the phishing kit was deployed. Not surprisingly, their target was PayPal. The Leaf PHP Mailer: The phishing page has all the features you would largely expect to see of a phishing C&C. The main […]
For the past three months, I’ve repeatedly received the same phishing email posing as a PayPal notification stating, “your account has been suspended,” attempting to steal my login details. The email arrives from “[email protected]” and looks very convincing for the average user. Here is the current phishing chain the threat actors are currently using in […]