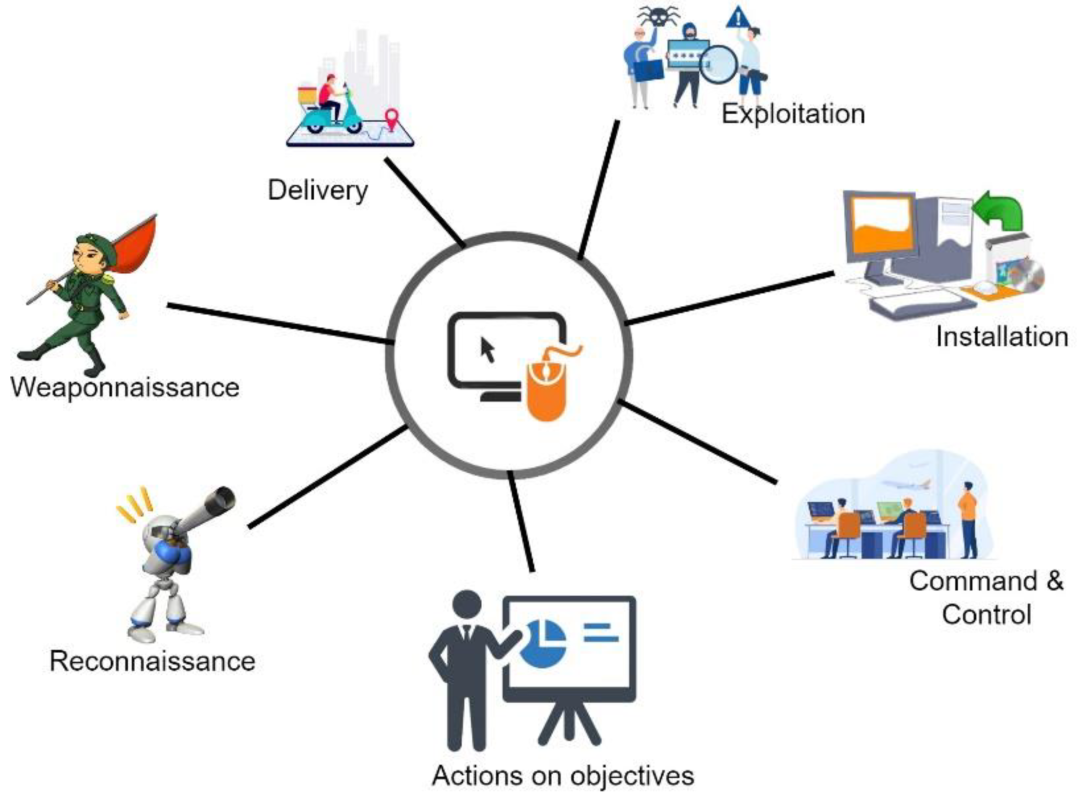
Practical queries for identifying malware infrastructure with FOFA. AsyncRAT Hardcoded Certificate Values cert.subject.cn=”AsyncRAT Server” || cert.issuer.cn=”AsyncRAT Server” – Link Cobalt Strike Default Certificate Values cert.issuer.cn=”Major Cobalt Strike” – Link cert.issuer.org=”cobaltstrike” – Link Amadey Bot Re-used certificate values cert.subject.cn=”desas.digital” – Link Quasar RAT Default certificate values. cert.subject.cn=”Quasar Server CA” – Link Laplas Clipper Certificate values and favicon hash. cert.subject.cn=”Laplas.app” – Link icon_hash=”1123908622″ – Link Sliver C2 Default Certificate values cert.subject.cn=”multiplayer” […]
Category Archives: Uncategorized
We’re all familiar with basic CyberChef operations like ‘From Base64,’ ‘From Decimal,’ and the occasional magic decode or XOR. But what happens when we need to tackle more complex tasks? CyberChef offers a range of advanced operations that are often overlooked in favor of Python scripting. Many are unaware of its more powerful features, such […]
This post will examine a Latrodectus loader that uses junk comments and WMI commands to obfuscate its functionality, ultimately downloading a remote .msi file. The sample operates in three distinct stages, which can be decoded using a combination of regular expressions and CyberChef. Obtaining the Initial SampleThe initial sample can be found on Malware Bazaar, […]
We recently discovered an impressive DNS analysis tool called Validin, which allows users to examine malicious domains and uncover related infrastructure through DNS records. This tool has proven to be invaluable, as most current infrastructure analysis tools tend to focus on pivoting from IP addresses, which operates quite differently from pivoting off domain names. The […]
In this post, we build on Microsoft’s 2022 ACTINIUM intelligence report by using passive DNS analysis to uncover additional domains that align with the patterns identified in the original report. By analyzing domain attributes such as IP addresses, registration dates, and subdomain patterns, we aim to identify potential new ACTINIUM infrastructure that may have emerged […]