In this blog, we will identify 36 Latrodectus phishing domains through passive DNS analysis of a domain reported on Twitter/X. The initial reported domain leverages 302 redirects to send users to a malicious or benign file. The URL in the 302 redirect is re-used across numerous domains; we can leverage this information to identify additional […]
Category Archives: Uncategorized
In this blog we will identify 6 malicious domains that are likely hosting MatanBuchus malware. We will identify these domains through the usage of hardcoded subdomains in the TLS Certificate of the initial shared domain. After leveraging the hardcoded subdomains, we will leverage registration dates and certificate providers to hone in on our final results. […]
Threat actors are known to monitor public reports and adjust any infrastructure they believe may be exposed. As intelligence analysts, it’s essential to stay updated on these changes and refine intelligence queries as needed. In this blog, we’ll look at a case where the creators of the Vultur banking trojan seem to have modified their […]
Threat actors frequently use domain-based infrastructure to support and execute malicious operations. When setting up these new domains, they often leave behind identifiable patterns, which can help in creating signatures that link new infrastructure to previously known activity. Developing these signatures can be challenging, and public documentation on the process is limited. Today, we’ll examine […]
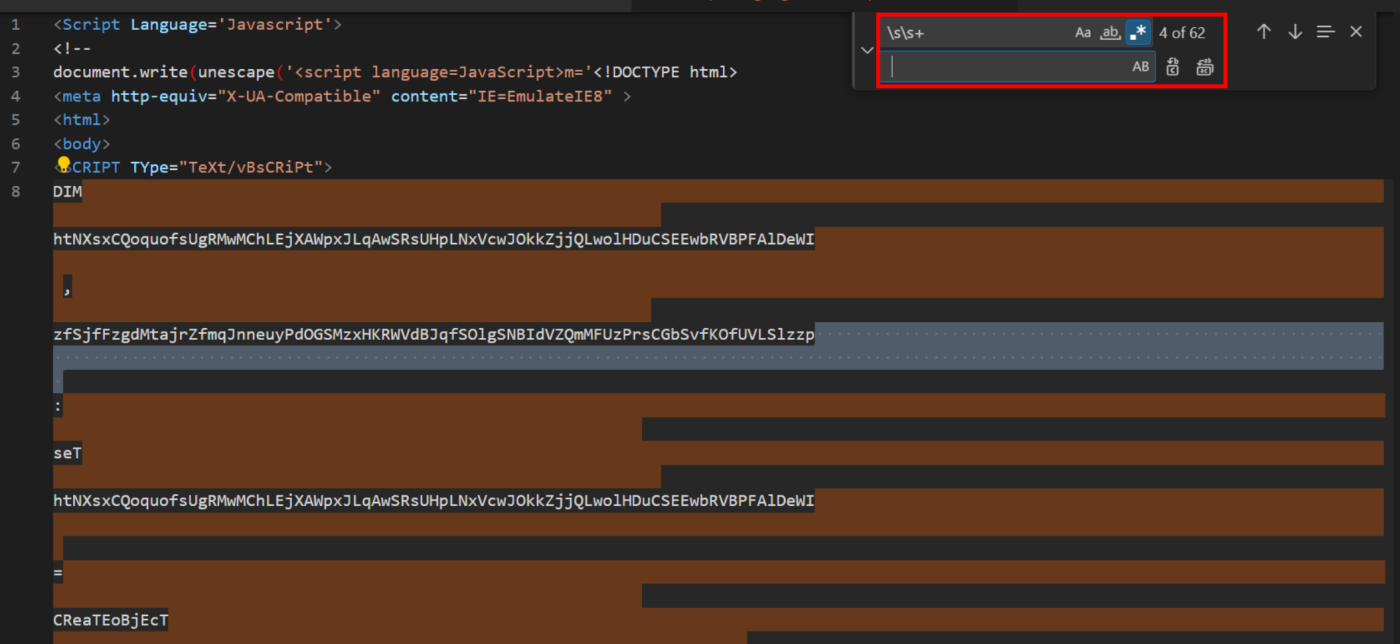
Introduction We recently encountered a short .HTA script on Malware Bazaar that was linked to the Cobalt Strike toolkit. The script utilises basic obfuscation that can be removed using CyberChef and a text editor. This blog will cover our decoding process, including how to decode the following obfuscation methods Original File The file used for […]