Threat actors are known to monitor public reports and adjust any infrastructure they believe may be exposed. As intelligence analysts, it’s essential to stay updated on these changes and refine intelligence queries as needed.
In this blog, we’ll look at a case where the creators of the Vultur banking trojan seem to have modified their domain naming patterns in response to a public threat intelligence report.
Using passive DNS tools, we’ll review historical domains to identify shared infrastructure and recurring patterns in naming conventions. These patterns will serve as pivot points, enabling us to uncover 13 new domains currently in use by the Vultur developers.
Initial Intelligence
The initial intelligence for this post originates from a fantastic Fox-it article describing Vultur Activity. The article goes into great detail about Vultur and its capabilities.
We won’t be covering the Vultur functionality here; instead, we will leverage the provided dropper distribution URLs to identify additional infrastructure.
The original dropper distribution URLs provided in the Fox-it article can be seen below.
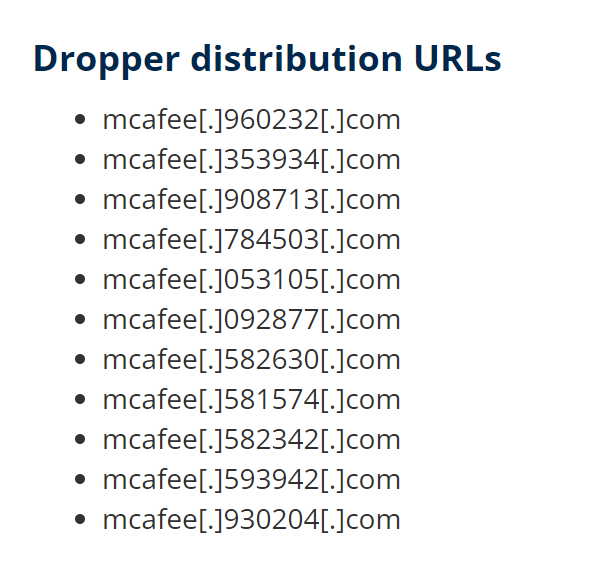
Initial Analysis Of Distribution URLs
The first step here is to gather basic intelligence on the initial reported URLs.
We will be leveraging Validin for this analysis. However, you are welcome to use any passive DNS tooling that you have access to.
The initial intelligence can be obtained using a bulk lookup, which provides a summary of the historical IP addresses associated with each initial domain.
We can leverage this to look for any commonalities in the historical IP addresses and establish an initial pivot point.
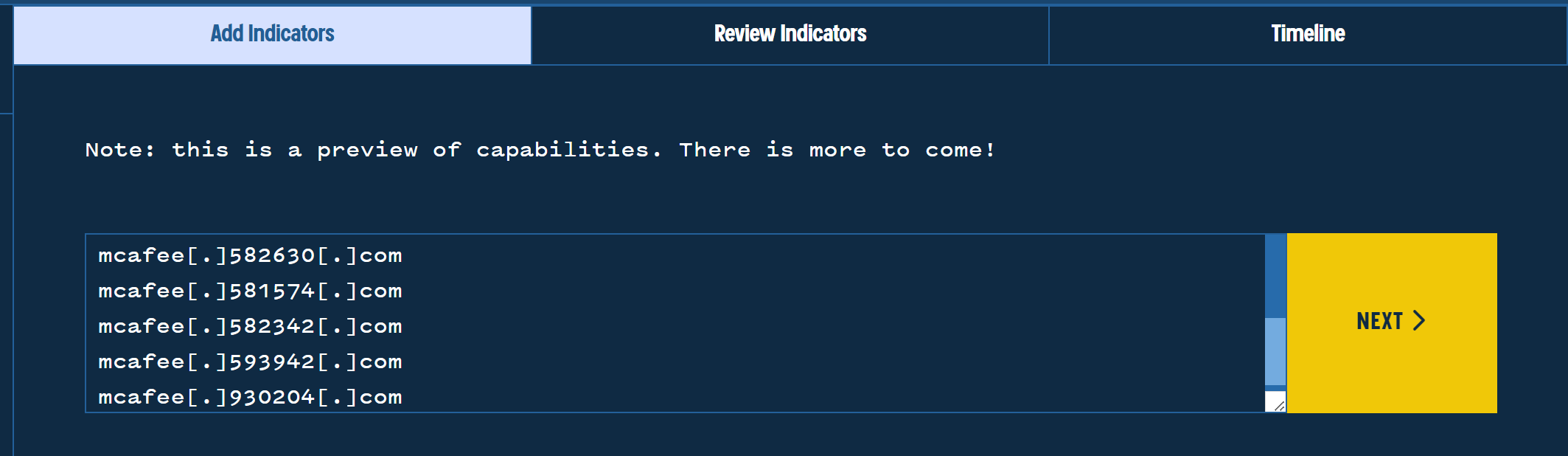
The bulk lookup returns the list of historical IPs for the domains, and immediately, we can see a commonality in historical IP addresses, which we can leverage as an initial pivot point.
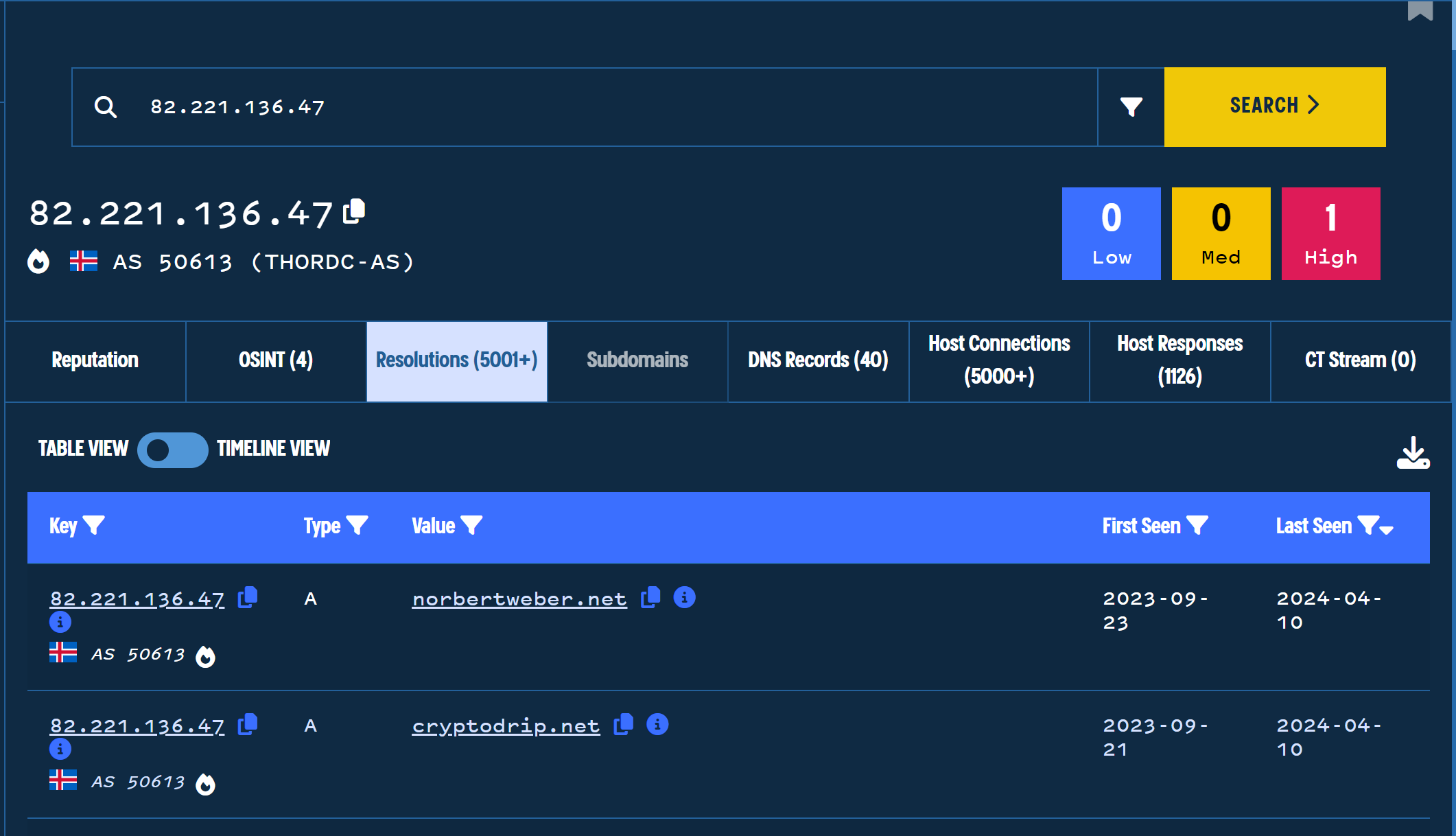
Below we can see that several of the domains have historically resolved to the same IP address of 82.221.136[.]47
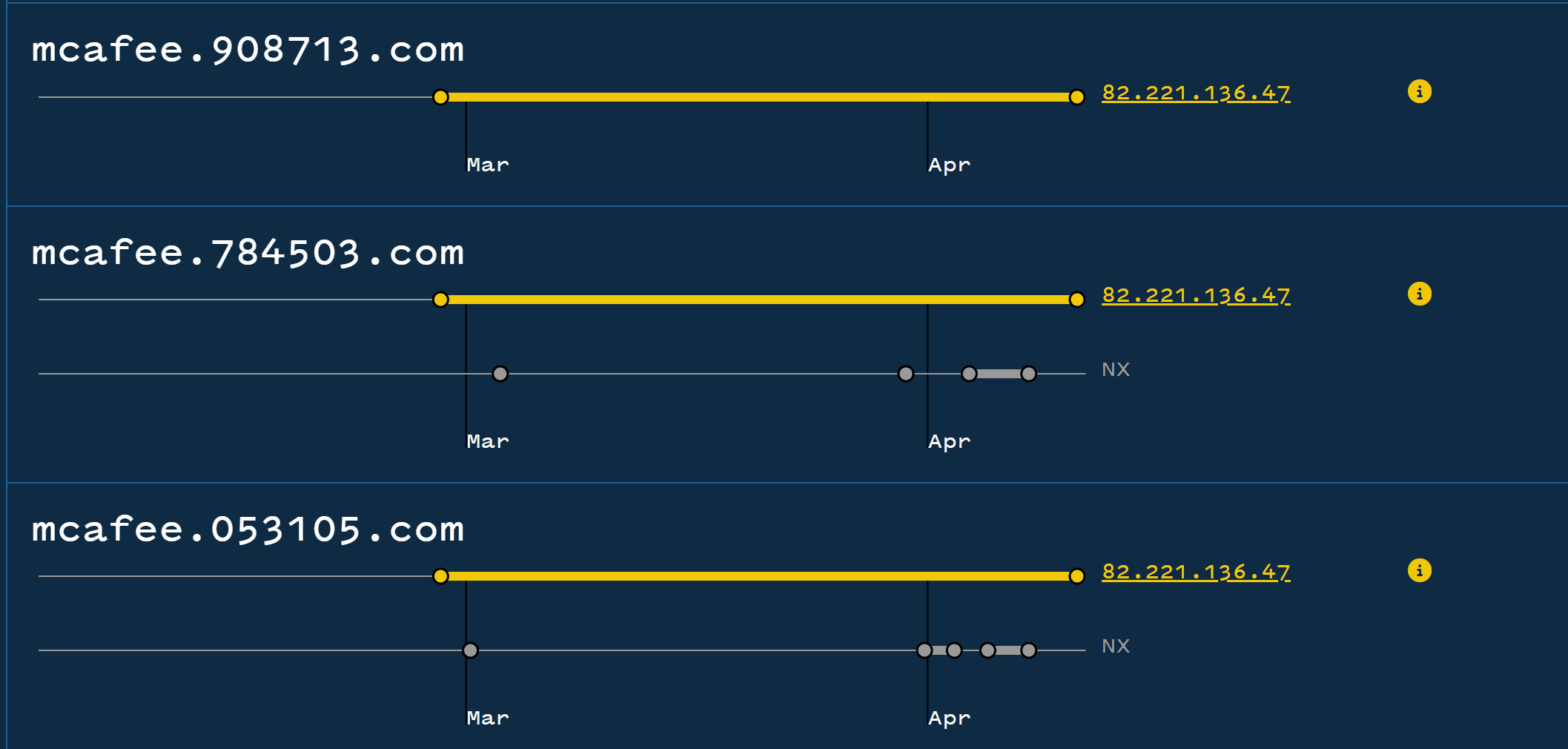
Initial Pivot on Common IP Address
With a common IP address identified across several (but not all) of the initial URLs, we can leverage this as a pivot point by searching on the IP address and viewing domains that have previously been associated.
In this case there are over 5000 domains associated. Indicating that this IP is likely a load balancer, proxy, or some kind of shared infrastructure.
This means that the IP itself may not be malicious, but there are malicious domains routing through it.
Pivoting on Subdomain
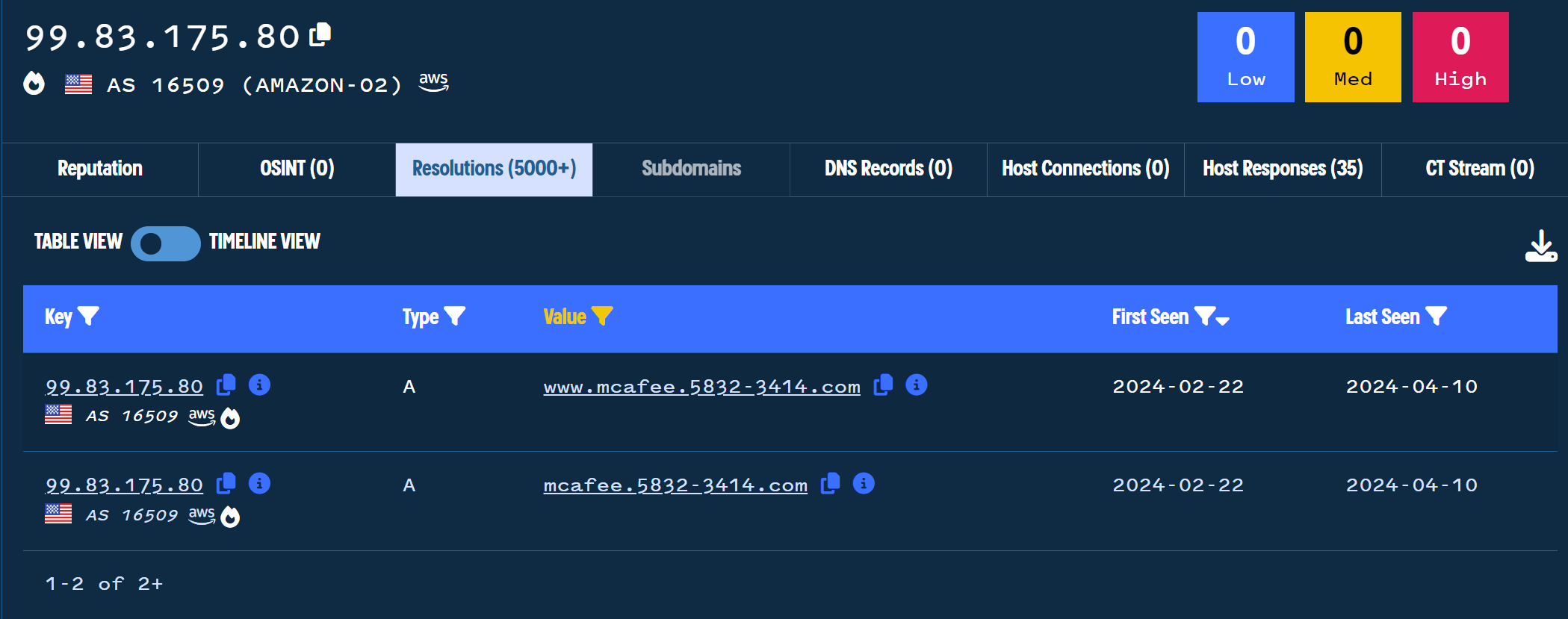
The initial intelligence shows that the malicious domains all contain the “mcafee” subdomain.
We can leverage this to narrow down our 5000 domains to only those that contain “mcafee”.
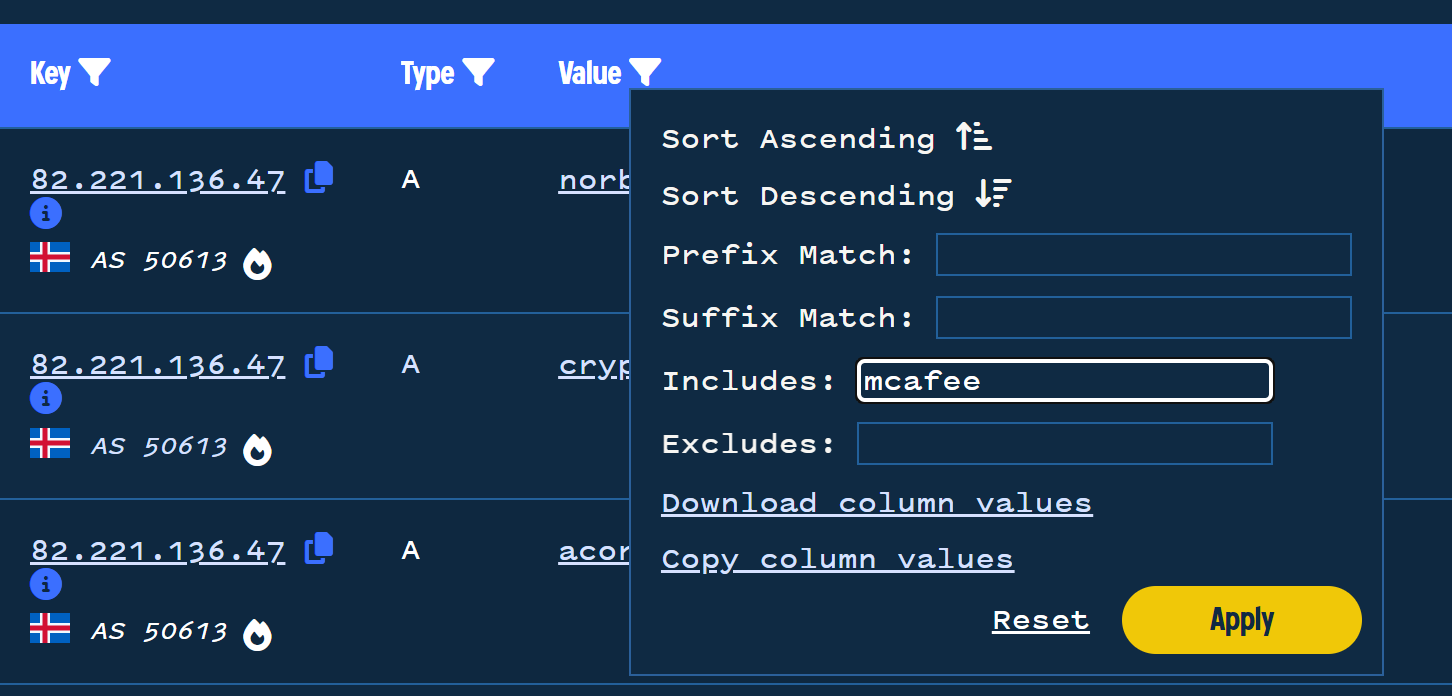
Applying the “mcafee” filter brings the 5000+ results down to only 24.
These 24 results show several of our initial domains and some new domains that leverage a hyphen between the numerical values.
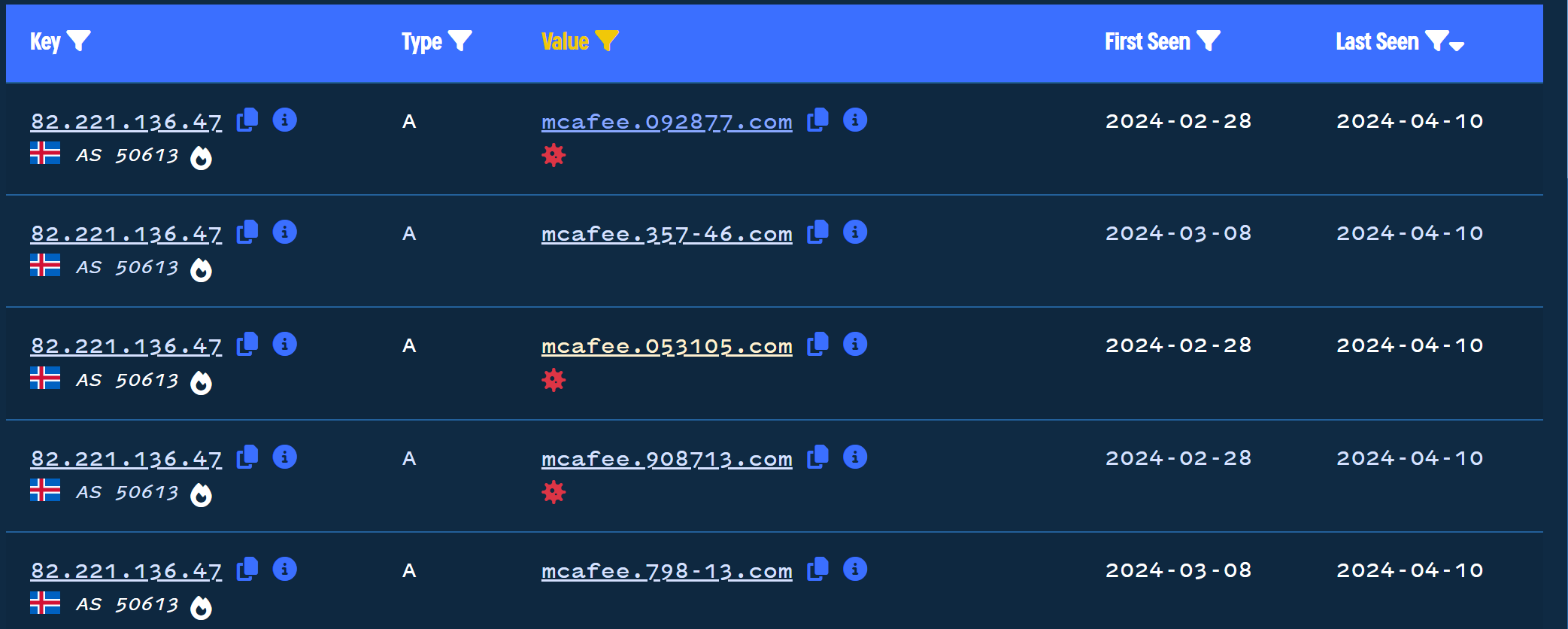
If we repeat this process for other observed IP addresses, we can see some of the same URLs provided in the initial report.
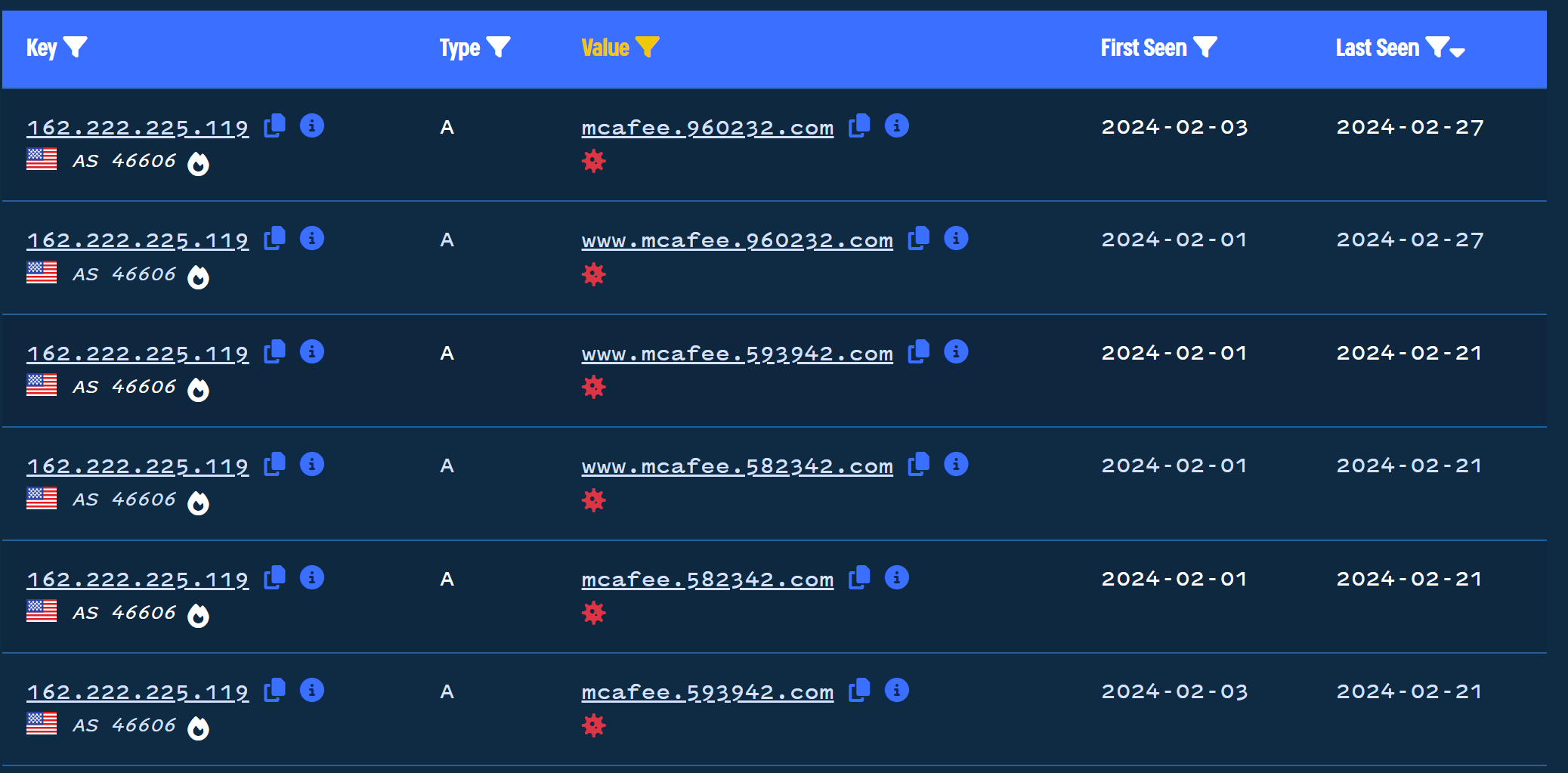
As well as some new results where the actor has increased the number of numerical values and included a hyphen.
This process can be repeated with the remainder of the IPs found in the initial bulk search. As well as with new IPs discovered in historical records during the investigation process.
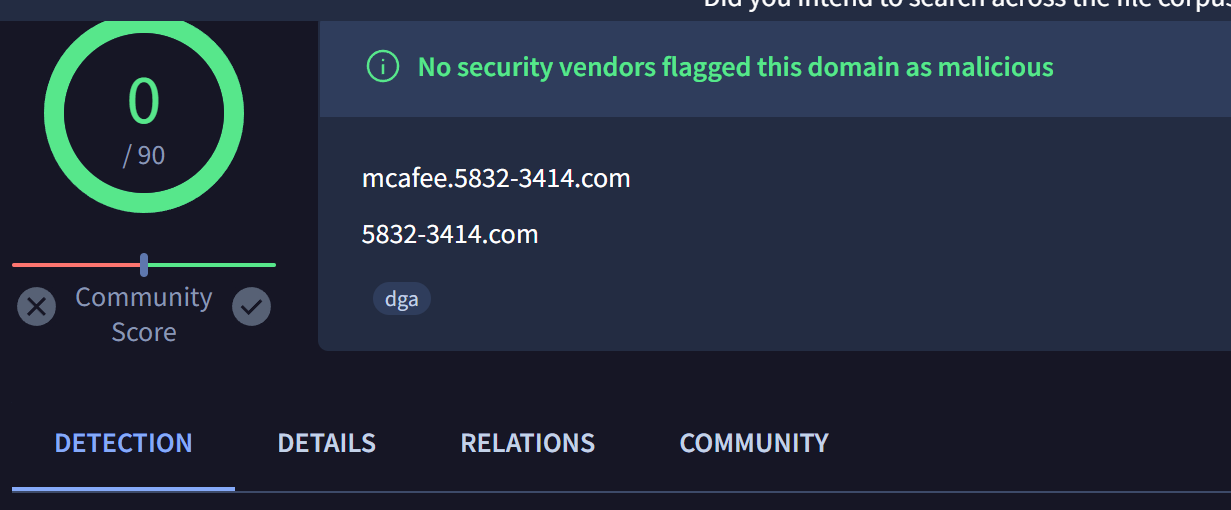
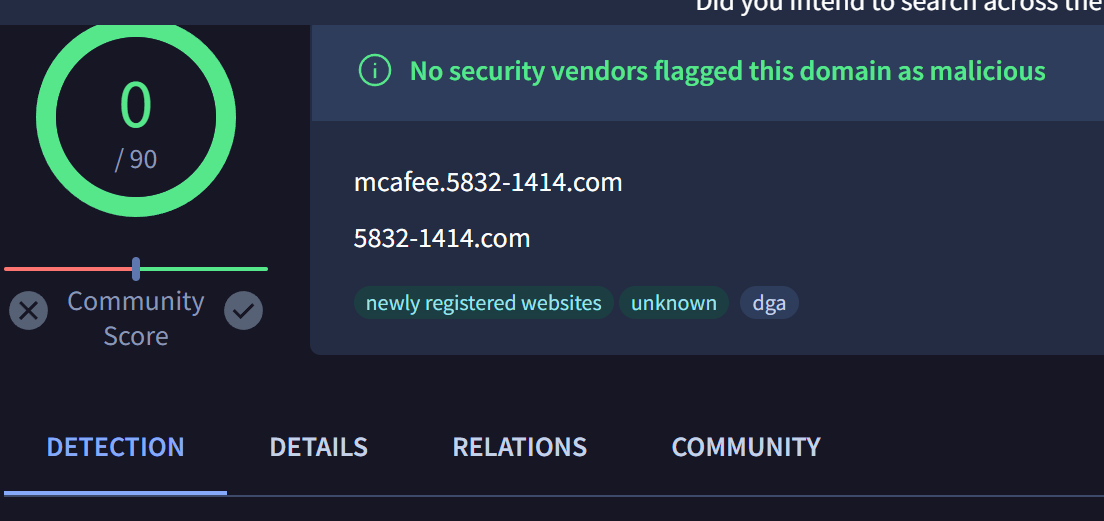
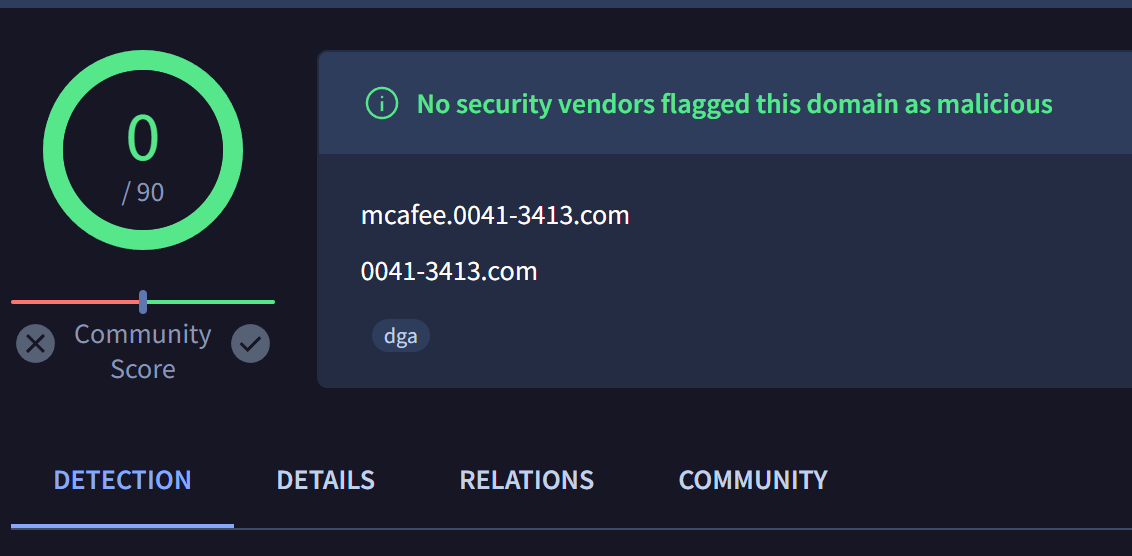
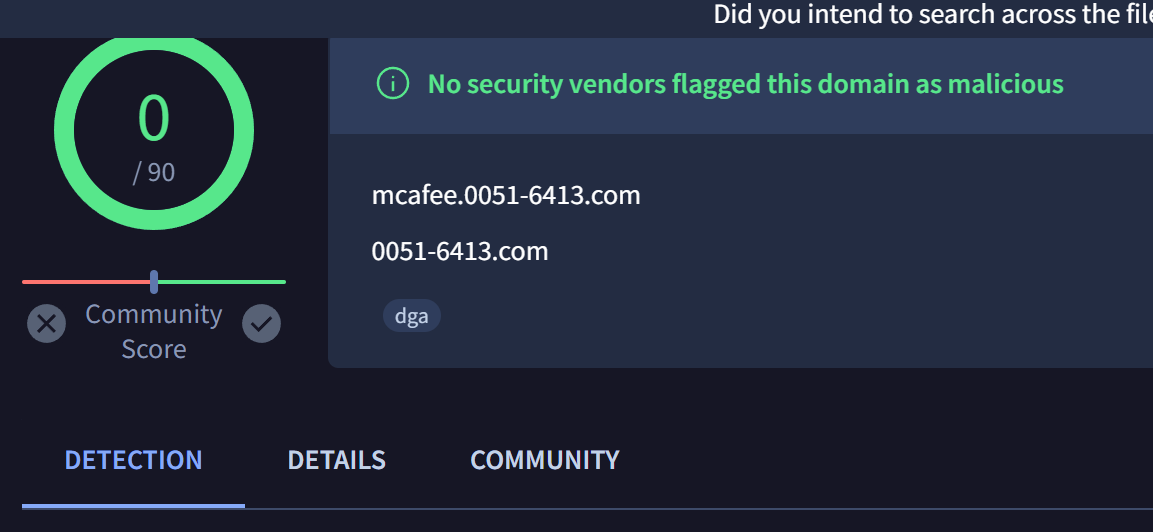
During our initial review, we were able to obtain 13 domains on the same infrastructure that were not included in the initial report.
As we did not check every IP address and resolve every domain, there are likely more out there that can be found with extra searching. You are welcome to try and find more using the free Community Edition of Validin.
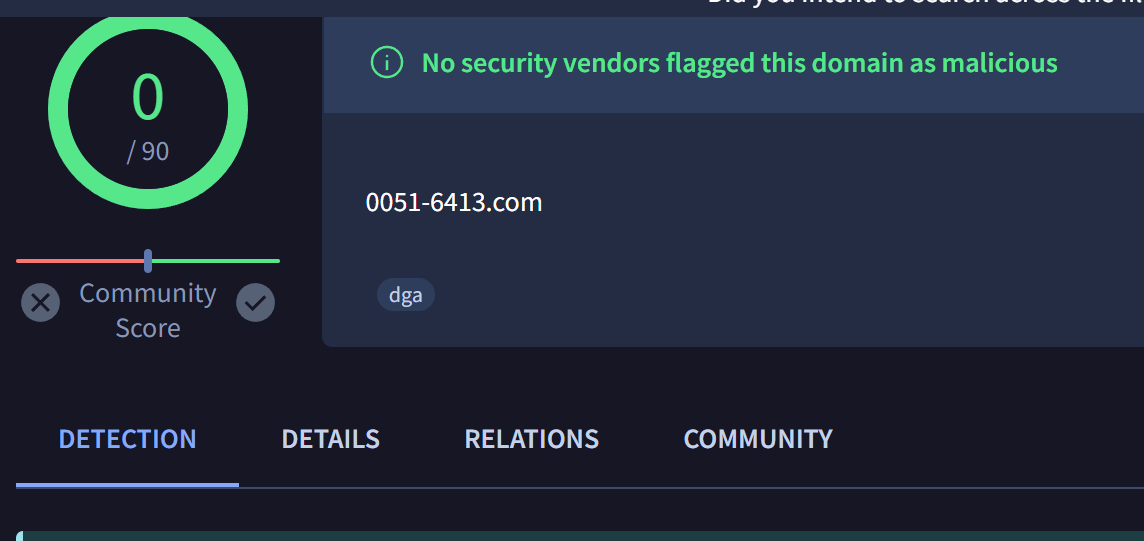
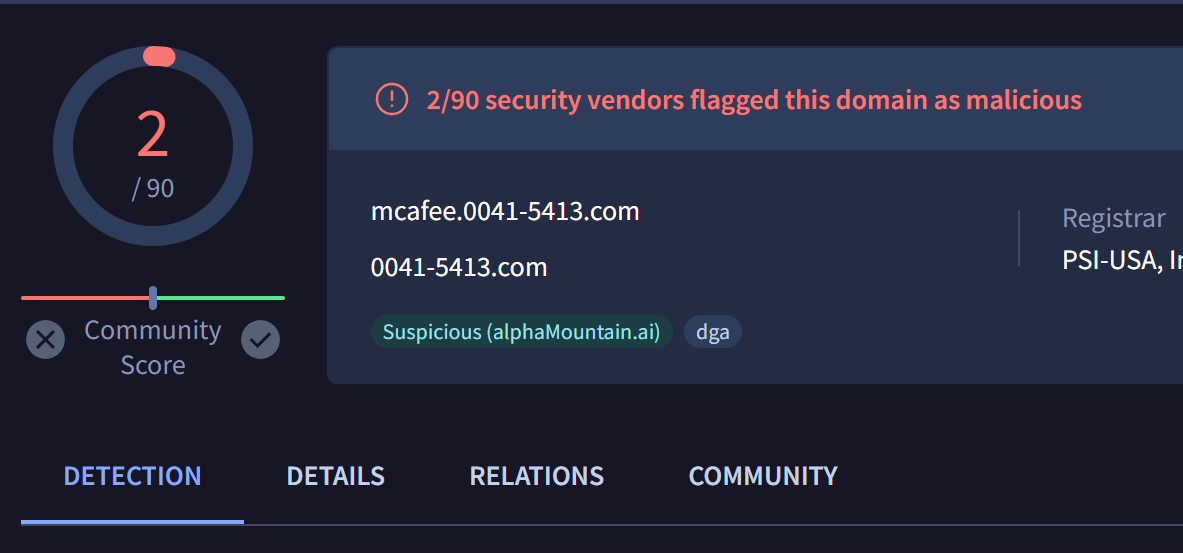
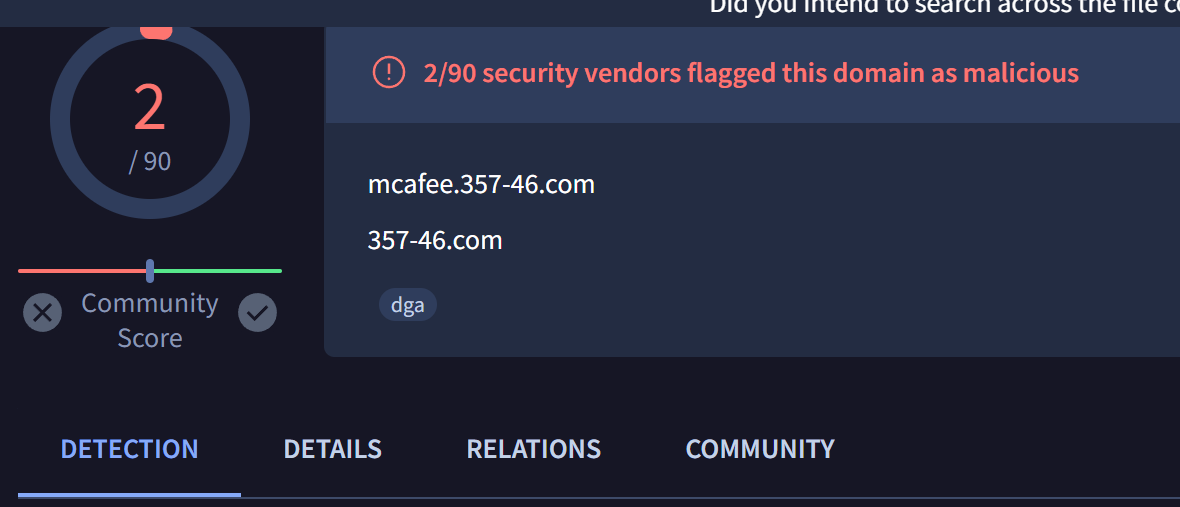
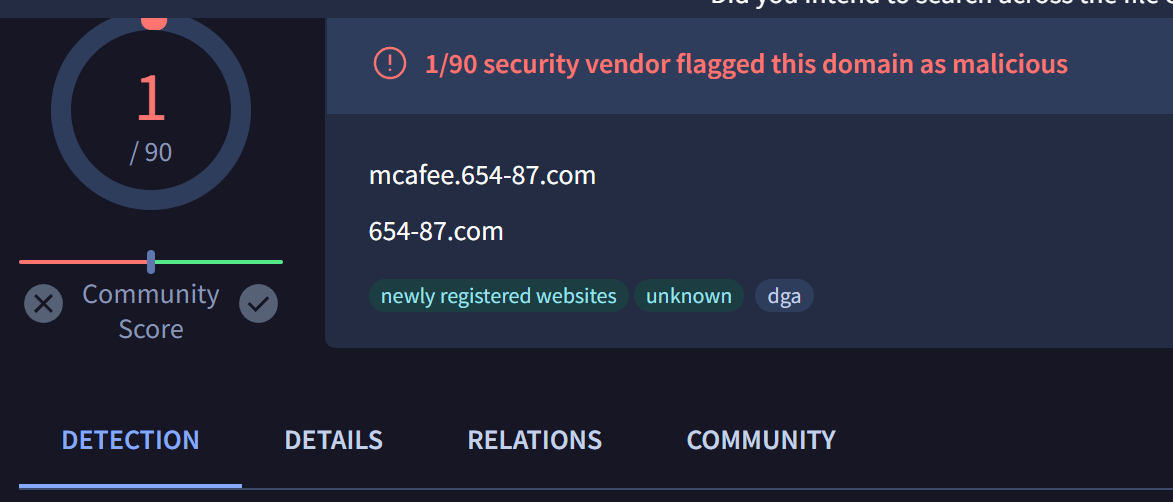
List of Malicious Domains
توضیحmcafee.0041-3413[.]com
mcafee.0041-5413[.]com
mcafee.0051-4413[.]com
mcafee.0051-6413[.]com
mcafee.357-46[.]com
mcafee.486-31[.]com
mcafee.5541-23[.]com
mcafee.5814-1601[.]com
mcafee.5832-1414[.]com
mcafee.5832-3414[.]com
mcafee.654-87[.]com
mcafee.789-20[.]com
mcafee.798-13[.]com
Virustotal Review